TLS Technicalities James
TLS Technicalities James
TLS Technicalities James
TLS Technicalities Synametrics Support
TLS Technicalities Synametrics Support
TLS Technicalities James
TLS Technicalities Synametrics Support
TLS Technicalities Anonymous
TLS Technicalities Synametrics Support
TLS Technicalities Synametrics Support
TLS Technicalities Anonymous
TLS Technicalities Synametrics Support
TLS Technicalities James
| From: | James |
|---|---|
| Date: | 8/1/17 11:00 AM |
| Topic: | TLS Technicalities |
| Type: | General Discussions |
| Post a follow up | |
|
Hello, Setup : Internet > Xeams > Exchange (Firewall mode) I was just wondering, is the communication between senders mail server and Xeams encrypted with TLS or is the encryption only occurring between Xeams and the internal exchange server? Whilst using starttls.com it seams Xeams is encrypting with proxied STARTLS commands but if Xeams in monitoring and checking contents of emails as they flow (according to your site: http://xeams.com/3Modes.htm ["In this mode Xeams acts like a firewall that sits in front of your corporate email server. Every in-bound email is checked by Xeams before it is forwarding the message to the actual email server."]
Thanks guys, excellent product. |
|
| Top |
| From: | James |
|---|---|
| Date: | 8/1/17 11:42 AM |
| Topic: | TLS Technicalities |
| Type: | General Discussions |
| Post a follow up | |
|
Just to confirm, I am completely aware that the contents of emails are not encrypted during TLS but the connection is. My concern is how can is email received during the TLS session during this proxy connection. Is it done at Xeams for receiving then re-started again between itself and exchange as a second session? Just a little detail please. Thanks. Thanks |
|
| Top |
| From: | James |
|---|---|
| Date: | 8/2/17 1:53 PM |
| Topic: | TLS Technicalities |
| Type: | General Discussions |
| Post a follow up | |
|
Hello Synametrics, Just a bump on the above support request. Thanks very much James |
|
| Top |
| From: | Synametrics Support |
|---|---|
| Date: | 8/3/17 9:29 AM |
| Topic: | TLS Technicalities |
| Type: | General Discussions |
| Post a follow up | |
|
Hi James, |
|
| Top |
| From: | Synametrics Support |
|---|---|
| Date: | 8/3/17 6:10 PM |
| Topic: | TLS Technicalities |
| Type: | General Discussions |
| Post a follow up | |
|
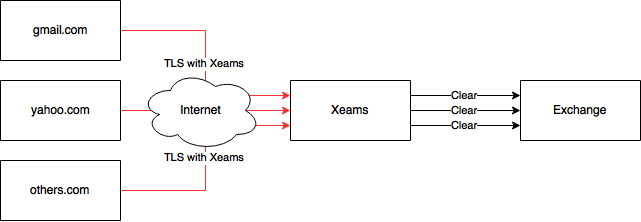
James, This is an excellent question. Thank you for asking. You are correct when you say Xeams acts as middleman when using the Proxy server. Since SSL does not allow a middleman, you MUST use a certificate on Xeams, not on Exchange. This way the communication between the sender's SMTP server and Xeams will be encrypted. See image below. In-bound Messages
When using the Proxy server, the certificate present on your Exchange never comes in picture. When two SMTP servers communicate with each other, one acts as a client and the other as a server. A certificate is only required by the end that is acting as a server. Therefore, STARTTLS will ONLY be used by sender's email server IFF you have installed a valid certificate in Xeams. When STARTTLS is not enabled in Xeams, the sender will send the message in clear. Out-bound MessagesWhen Xeams needs to send messages out to another SMTP server it acts as a client. Since a certificate is NOT needed when acting as client, Xeams will always use STARTTLS even if it is not enabled for incoming. In this case, the communication between Exchange and Xeams may or may not be enabled. Out-bound communication with, for example, gmail.com will always be enabled since Google supports STARTTLS
Let us know if you need further explanation. |
|
| Top |
| From: | James |
|---|---|
| Date: | 8/10/17 9:50 AM |
| Topic: | TLS Technicalities |
| Type: | General Discussions |
| Post a follow up | |
|
Thank you for your support and response in helping to understand the procedure however I think there is a slight confusion. If you are presently using Xeams on your demo lab and have both a certificate installed in exchange and in Xeams please browse to checktls.com and give it a try yourselves. I've attached a snippet below on what exactly is proxied across. Exchange seems to be doing the TLS and not Xeams. If you take a closer look you will see that Exchange is in fact explaining to the remote server "we are TLS ready" not Xeams. If you continue further down you will also see the connection is proxied with the AUTH commands and SIZE commands of the exchange server. The exchange server is replying back and serving the certificate through the proxy which is incorrect according to RFC standards.
|
|||||||||||||||||||||||||||||||||||||
| Top | |||||||||||||||||||||||||||||||||||||
| From: | Synametrics Support |
|---|---|
| Date: | 8/10/17 10:15 AM |
| Topic: | TLS Technicalities |
| Type: | General Discussions |
| Post a follow up | |
|
James, What is the IP address of your server? Is it possible for you to call us or send us an email. Explaining this over the phone will be a lot easier. Our number is 609-750-0007 - dial 2 for support. In any case, I am going to try to explain this for other viewers. The SSL encryption occurs at the network layer. When a sender (checktls.com) tries to connect, a TCP/IP socket is created between CheckTLS and Xeams. This socket has no idea about Exchange. Once the connection is established, Xeams will open another socket to your Exchange. Now Xeams acts as a middleman. Whatever CheckTLS sends, Xeams forwards that request to Exchange. When Exchange replies back, Xeams sends most of the reply back. I say "most of the reply" back because some extensions supported by Exchange are not supported by Xeams and therefore, it hides them. This is precisely the reason why you see a 250-STARTTLS as part of the EHLO command. Try opening a connection using telnet directly to your Exchange and you will see additional verbs as part of EHLO that are suppressed by Xeams. Xeams does not filter the Internal Server Name, SIZE and few other parameters coming back from Exchange and therefore, you see them verbatim on the other side. This does not mean the SSL communication is between checktls.com and Exchange. The actual encryption is only between checktls and Xeams.
|
|
| Top |
| From: | Anonymous |
|---|---|
| Date: | 8/11/17 10:08 AM |
| Topic: | TLS Technicalities |
| Type: | General Discussions |
| Post a follow up | |
|
Thank you for your response. I will get an email out or call you a little later.
If this was the case, why are you allowed to use the same certificate from a different server detailed on your site here [http://www.xeams.com/using-iis-cert.htm] with no mention that the the certificate name must include the Xeams server as an alternative name? The TLS session would fail on validation tests if the hostname used in your IIS certificate server example above was different to your Xeams server hostname. Your site needs to mention this or at the very least mention explain that only wildcard certificates would work using those instructions. Give it a try. Export a certificate with an alternative hostname [server-name] and import it into your Xeams lab server then run a TLS session with Xeams and let me know what you guys get. In theory it would work if both machines had the same name OR it was on a SAN certificate OR you used a wild card but thats all. Another example is if you shutdown your Exchange server and run the same test at checktls.com you will find that the maximum the senders server can do is connect to Xeams but no TLS will take place and the test will fail. This is another indicator that Xeams is not properly implementing TLS according to standards or for that matter according to the way your explanation is. I am a little sceptical about the security of certificates being installed on Xeams servers. |
|
| Top |
| From: | Synametrics Support |
|---|---|
| Date: | 8/11/17 10:46 AM |
| Topic: | TLS Technicalities |
| Type: | General Discussions |
| Post a follow up | |
|
James, You are correct - it is NOT one stateful connection. They are two different connections. One SSL certificate can be used on different servers, provided the host name matches. If you have a wild-card cert, that takes care of the host name problem as well. The reason we mention using "wildcard" is because the page assumes the certificate on your IIS is probably for www.yourdomain.com and the host name of your mail server will be something like mail.yourdomain.com . Bottom line: same certificate you use on Exchange can be used in Xeams, provided the host name problem is solved. If the shutdown Exchange, the Proxy server in Xeams will also shutdown. That is because as soon as a EHLO is sent from CheckTLS, Xeams will try to open another socket to Exchange. If that second socket cannot be opened, Xeams will display an error complaining server is temporarily unavailable. This does NOT mean TLS is not working. TLS starts AFTER the EHLO command. If EHLO fails, no TLS will every occur. I think you are confusing between SSL and STARTTLS. The port for SSL is typically 465. Any communication on this port will be 100% encrypted (even the HELO/EHLO). STARTTLS on the other hand starts with plain non-encrypted communication, checks if the receiving server supports STARTTLS (which is an option returned by EHLO command) and then upgrades the existing socket to SSL. This will be evident from looking at SMTPOutboundConversation.log . Try sending an email to gmail.com and then look at that log in Xeams. The EHLO command is sent twice. The first call will be in plain and the second will be encrypted. Additionally, gmail.com's server will only advertise STARTTLS in the first call. The second call, which is already encrypted, will not have a 250-STARTTLS as part of its EHLO results.
|
|
| Top |
| From: | Synametrics Support |
|---|---|
| Date: | 8/11/17 11:02 AM |
| Topic: | TLS Technicalities |
| Type: | General Discussions |
| Post a follow up | |
|
I forgot to answer a couple of questions: why is the connection NOT encrypted from the start? There is a historic reason for this. When email first started, SMTP servers used to communicate on port 25 and there were no SSL certificates. Later on port 465 was introduced for SSL. However, many servers kept communicating on port 25 without encryption. There was a need to use SSL on port 25 without breaking the existing communications. That is when STARTTLS was introduced, which has the ability to start with non-encrypted communication and later upgrade the same socket to encrypt. You said: A simple sniffing tool sitting between Xeams and Exchange will be able to watch the communication. This is correct but there is more to it:
|
|
| Top |
| From: | Anonymous |
|---|---|
| Date: | 8/17/17 10:44 AM |
| Topic: | TLS Technicalities |
| Type: | General Discussions |
| Post a follow up | |
|
Hi, I'll answer both posts in this one; 1. TLS starts after HELO - agreed and understand. 2. "I might be confusing SSL and TLS" - Is there a need for those sort of remarks? (port 465, upgrading connection, etc.) 3. If a message is considered good, Xeams will create a brand new connection to Exchange. This new connection will be visible through SMTPOutboundConversation.log and will use STARTTLS if supported by Exchange. - Can you please explain this a little further with an illustration. From what I gather you are saying the below is occurring however your illustration above shows the connection to Exchange for last leg delivery is plain text?
gmail, yahoo, etc. > Xeams (TLS) > Check if From and RCPT valid with Exchange & AD > No > Drop local connection to Exchange > Drop external connection to remote server and don't filter at all.
|
|
| Top |
| From: | Synametrics Support |
|---|---|
| Date: | 8/17/17 11:24 AM |
| Topic: | TLS Technicalities |
| Type: | General Discussions |
| Post a follow up | |
|
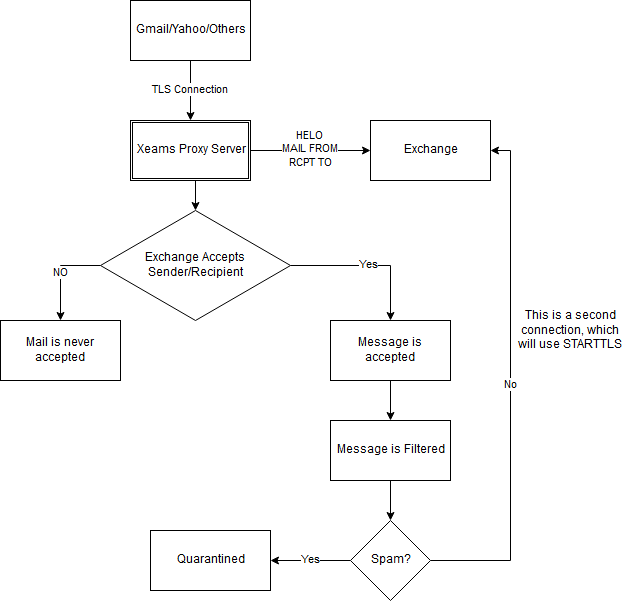
James, I'd like to first apologize for some confusion that got created because I misunderstood your post. I interpreted your wildcard comment as a question instead of a recommendation and therefore, answered it incorrectly. We have added your suggestion to http://xeams.com/using-iis-cert.htm . Let us know if we should further modify it. The link in the earlier post ends with a ] which resulted in a 404 on your end. Answer 2: Again I apologize. I did not mean any disrespect. Answer 3: Here is a flow chart.
Answer 4: Yes, but only if all of the following conditions are true:
Note that until recently, AD was only used when using the regular SMTP server. However, Microsoft changed the way they reject invalid users in Exchange 2013 and 2016. They no longer reject invalid users after RCTP TO. Instead, they reject the email after DATA, which breaks the logic in Xeams. Therefore, we had to add AD integration for Proxy Server. Answer 5: This is partially answered by #4. If you are installing this on a large scale, I'd recommend NOT using the Proxy Server but using the Regular SMTP Server for both inbound and outbound. I say that because:
I also recommend checking http://www.xeams.com/clustering.htm to see how to use Xeams in a large environment.
|
|
| Top |
| From: | James |
|---|---|
| Date: | 9/5/17 5:07 PM |
| Topic: | TLS Technicalities |
| Type: | General Discussions |
| Post a follow up | |
|
Hello Again,
Regards,
|
|
| Top |