Tricky Sender A custom filter
On December 05, 2017, Sabri Haddouche published an article on https://www.mailsploit.com/index explaining how to craft emails that can easily forge the sender's identity. He found bugs in 33 different products, including the popular ones from Microsoft, Apple, and Mozilla.There are some important points to note regarding this discovery:
- The actual forgery is embedded in the FROM header of the actual message
- It can be sent containing a valid DKIM signature and can also originate from a designated IP. This means neither SPF, DKIM or DMARC will fail
- Most email servers will not know/care about this mechanism since the MAIL FROM in the envelope is not forged
What can you do
Although it can take some time before every client is updated, you can certainly block these messages from getting into your network by using the latest version of Xeams. The exact build number containing this fix is 5968.How to confirm if the fix is working
Sabri is kind enough to not only point out the problem but also created a demo to test it. You can generate 14 emails containing different variations of the problem. Xeams should be able to catch them and assign a score.Another Variation
Consider the following email header, which is yet another variation of a tricky sender.From: "John Doe <john.doe@example.com> " <john.doe@spammers.com> To: Jane Doe <jane.doe@example.com> Message-ID: <1949119394.0.155994902700@exchange.local> Subject: Overdue invoice - please pay today MIME-Version: 1.0 Content-Type: text/html; charset=UTF-8 Content-Transfer-Encoding: 7bitMultiple tricks are used in the above example:
- The email address appears twice in the FROM header.
- The second email matches with the SMTP Envelope, which does not have any SPF or DMARC
- The name of the sender also contains an email address following by a bunch of SPACE characters
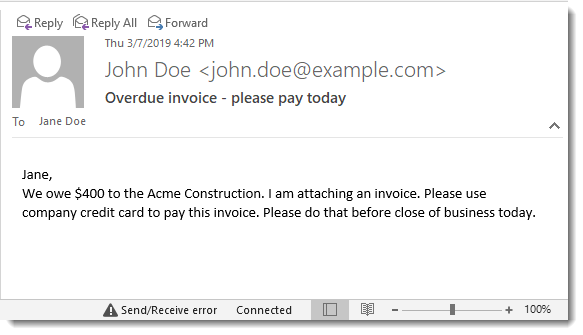 Since the sender put empty SPACE characters in the FROM header, the other address is being displayed outside the window
boundary, making the reader think message came from John Doe, with is actual email.
Since the sender put empty SPACE characters in the FROM header, the other address is being displayed outside the window
boundary, making the reader think message came from John Doe, with is actual email.
