Document information
| Document ID: | 5224 |
|---|---|
| Subject: | SMTP Connections vs Email ratio |
| Creation date: | 7/3/18 11:00 AM |
| Last modified on: | 4/6/22 10:05 AM |
SMTP Connections vs email ratio
It is very common to see many clients connecting to your SMTP server but not deliver any email. Starting from version 6.5, Xeams displays a graph plotting the ratio between the two events.Consider the image below as an example:
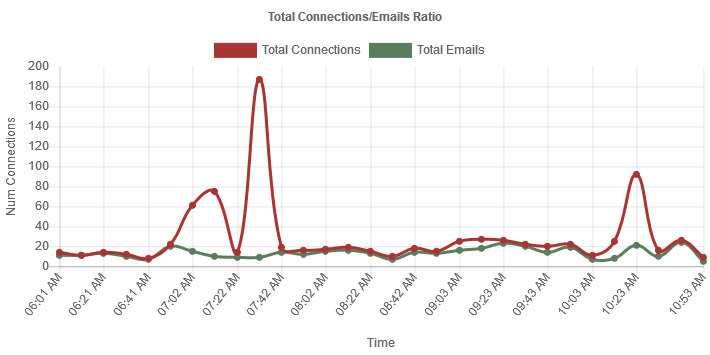 Ideally, every connection to your SMTP server should result in an email. In that case,
both lines should draw themselves very close to each other. Reality is often different from
this ideal situation.
Ideally, every connection to your SMTP server should result in an email. In that case,
both lines should draw themselves very close to each other. Reality is often different from
this ideal situation.
The graph above shows around 190 new connections around 7:30 AM but only 15 emails. This indicates someone connecting to the server but not delivering any emails. There are several reasons for such behavior:
- Someone is trying to send emails to invalid users
- Someone is trying to guess user id/passwords on your server
- A watch dog service is trying to check if your SMTP server is up and running
- A connection problem related to the network. Probability of this problem is very low if you only see one or two spikes in the graph.
Further Investigation
A sudden spike in the graph around 7:30 AM indicates a potential problem. To investigate, we will have to check the SMTPConversation.log (SMTPProxyConversation.log if you're using the Proxy server for inbound emails) for further information. Use the following steps:- Log in as admin
- Click View Logs under Tools menu
- Select SMTPConversation.log for the file and type
New connectionin the Search field. - The following screen will display new connections, which will look something like:
2018-07-03 07:36:54,439 - [ 36556595] ************ New connection from: 114.99.26.246 2018-07-03 07:36:55,829 - [ 36556596] ************ New connection from: 114.99.26.246 2018-07-03 07:36:57,204 - [ 36556597] ************ New connection from: 114.99.26.246 2018-07-03 07:36:58,595 - [ 36556598] ************ New connection from: 114.99.26.246 2018-07-03 07:36:59,986 - [ 36556599] ************ New connection from: 114.99.26.246 2018-07-03 07:37:01,329 - [ 36556600] ************ New connection from: 114.99.26.246 2018-07-03 07:37:02,908 - [ 36556601] ************ New connection from: 114.99.26.246 2018-07-03 07:37:04,361 - [ 36556602] ************ New connection from: 114.99.26.246 2018-07-03 07:37:05,798 - [ 36556603] ************ New connection from: 114.99.26.246 2018-07-03 07:37:07,298 - [ 36556604] ************ New connection from: 114.99.26.246 2018-07-03 07:37:08,814 - [ 36556605] ************ New connection from: 114.99.26.246 2018-07-03 07:37:10,220 - [ 36556606] ************ New connection from: 114.99.26.246 2018-07-03 07:37:10,689 - [ 36556607] ************ New connection from: 92.207.67.197 2018-07-03 07:37:11,626 - [ 36556608] ************ New connection from: 114.99.26.246 2018-07-03 07:37:13,017 - [ 36556609] ************ New connection from: 114.99.26.246 2018-07-03 07:37:14,486 - [ 36556610] ************ New connection from: 114.99.26.246 2018-07-03 07:37:15,876 - [ 36556611] ************ New connection from: 114.99.26.246 2018-07-03 07:37:17,267 - [ 36556612] ************ New connection from: 114.99.26.246 2018-07-03 07:37:18,705 - [ 36556613] ************ New connection from: 114.99.26.246 2018-07-03 07:37:20,205 - [ 36556614] ************ New connection from: 114.99.26.246 2018-07-03 07:37:21,595 - [ 36556615] ************ New connection from: 114.99.26.246 2018-07-03 07:37:23,033 - [ 36556616] ************ New connection from: 114.99.26.246 2018-07-03 07:37:24,486 - [ 36556617] ************ New connection from: 114.99.26.246 2018-07-03 07:37:25,923 - [ 36556618] ************ New connection from: 114.99.26.246
- Notice that most connections are coming from
114.99.26.246 - The number in square brackets is called an LCID (log correlation ID), which can be used to view communication
for a single connection. Copy one of these numbers, let's say
36556595, to your clipboard - Click the Back button on your browser and search for this number instead.
- The following screen displays log lines that look something like:
2018-07-03 07:36:54,439 - [ 36556595] ************ New connection from: 114.99.26.246 2018-07-03 07:36:54,658 - [ 36556595] C --> helo fxdce 2018-07-03 07:36:54,658 - [ 36556595] S <-- 250 114.99.26.246. Please to meet you 2018-07-03 07:36:54,876 - [ 36556595] C --> auth login 2018-07-03 07:36:54,876 - [ 36556595] S <-- 500 Syntax error, command unrecognized. 2018-07-03 07:36:55,095 - [ 36556595] ~~~~~~~~~~~~ Connection Terminated (656:999999) Unexpected input termination. Connection terminated without a graceful QUIT. - The most important command is highlighted in red above, which shows the client is trying to send a login, even though SMTP authentication is not supported. This is a clear indication of someone trying to guess a user id/password from 114.99.26.246
Preventing Unauthorized Access
You can certainly block certain IP address from connecting to your server. However, chasing after different IP addresses will drive you crazy. Click here for some tips on how to prevent users from guessing passwords.Add a comment to this document
Do you have a helpful tip related to this document that you'd like to share with other users?
Important: This area is reserved for useful tips. Therefore, do not post questions here. Instead, use our public forums to post questions.
