URL Sandbox
Starting v7.0, Xeams can optionally rewrite every URL inside an incoming email from the Internet, allowing a user to inspect the URL's contents before clicking the actual link.
How it Works
Consider an example where a user gets an email asking them to log in to their email account and change password because of a new company policy.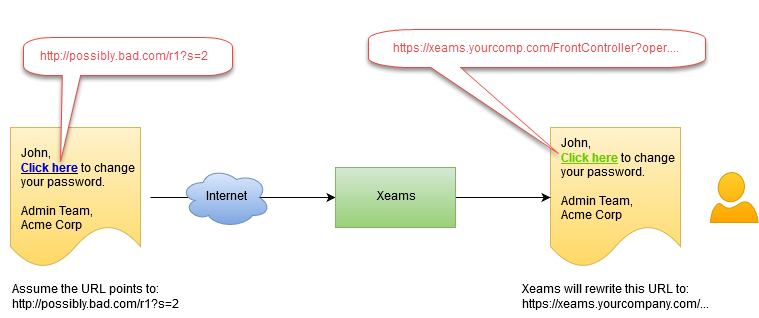
Often emails are composed to give the end-user an impression it came from a legitimate source. Disaster can strike if the recipient clicks the link, which could end up in downloading malicious files or capture user's passwords.
Every URL inside an incoming email will be modified so the user's click goes through your Xeams server, which will analyze the link for any malicious redirects or downloads. This method works regardless of the device where email is viewed.
Configuring Sandbox
- Log in as admin
- Click Sandbox Configuration under Filter Management
- Enable Sandbox
When Does URL Sandboxing Occur?
It occurs on three occasions:- Inbound emails are received with score higher than the configured threshold. Users will see the sandboxed version of the link when viewing messages in their email client, such as Outlook or Thunderbird
- Messages are viewed through Message Repository in the Admin Console. When logged in as admin, you will have a choice to toggle sandbox setting when viewing messages. Non-admin users cannot toggle this setting. They will inherit the configuration set by administrator.
- Administrator can run any URL inside the sandbox by clicking the Tools menu in the Admin Console.
Important Tips
- URL rewriting only occurs for inbound messages. Outbound emails are not modified
- Only HTML messages are modified.
- Administrators can optionally chose not to use sandbox for trusted domain or emails scoring below a certain threshold.
