Document information
| Document ID: | 5396 |
|---|---|
| Subject: | Dangerous malware disguised as Excel Spreadsheet |
| Creation date: | 10/16/20 4:33 PM |
| Last modified on: | 1/12/22 2:47 PM |
Dangerous malware disguised as Excel Spreadsheet
If you are one of the millions of people who use email in your day-to-day business functions you are probably aware of the dangers of malware. Hackers are always on the advance with ever increasing ways to target and infect unsuspecting users with malicious programs. Recently it has come to light that they are using new, and very common, tools to accomplish this task, and that is through Microsoft Excel. This article talks about how they are able to use Excel and steps you could take to stay safe.
How it works
The attacker will start off with a standard phishing email. This is a relatively harmless email, containing a few sentences asking the user to open the attached spreadsheet. These are designed to seem as if they are coming from a legitimate business associate.
Inside the spreadsheet it will appear, at first glance, to be a normal spreadsheet, with a message telling you to click on the enable editing button to view the sheet.
This is where it gets dangerous
- The opening page of the spreadsheet will have a message similar to the below asking your user to click on the enable editing button.
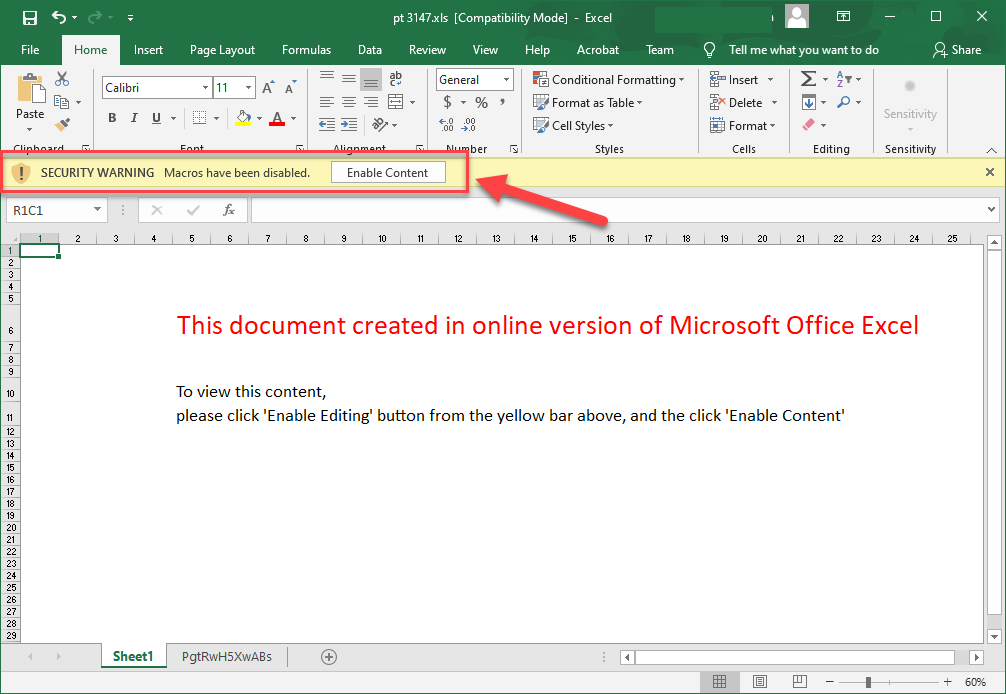
- After enabling editing, the sheet will also ask to enable macros.
- The warning message and corresponding button for enable editing are visibly similar to the enable macros button. This is a trick used to fool users who quickly click the button thinking it is to enable editing again.
- If you notice, there is a second sheet with a random name.
- At first glance, sheet two appears blank. However, there is a script that is hidden hundreds of pages down into the sheet.
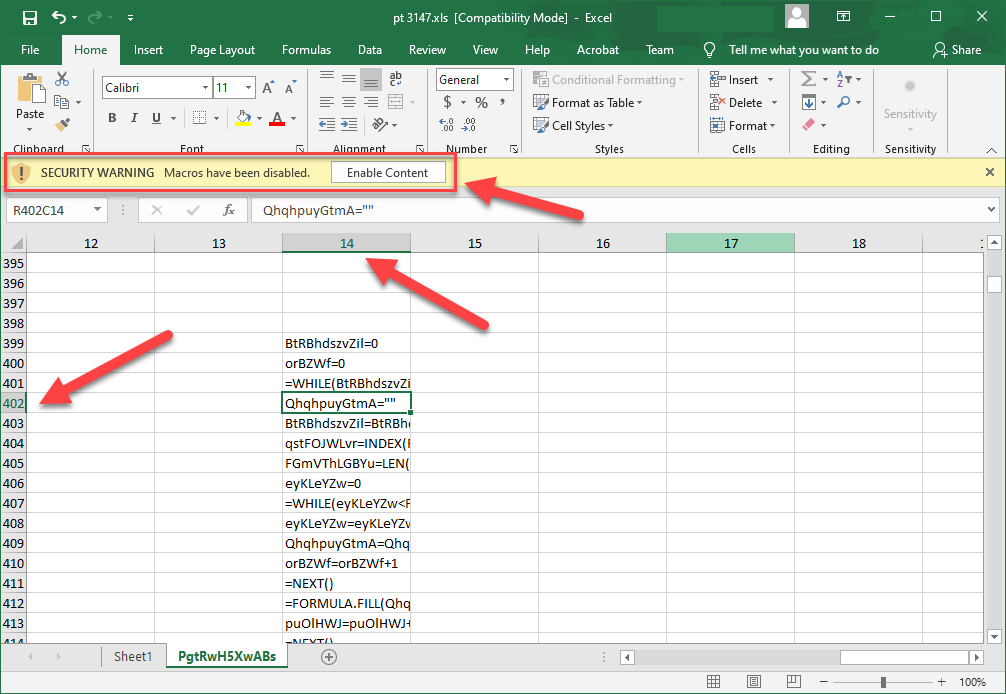
From here, the macro will dynamically build a URL that it will fetch a virus from. Since you enabled editing, the virus will be downloaded directly to the computer, and typically circumvent most antiviruses. From here, the attacker will most likely have remote access to your machine.
Prevention
The best approach to prevent these types of attacks is to stop them at the SMTP level. By doing this, you completely eliminate User Error from the equation. In order to accomplish this, you will need a powerful SMTP server such as Xeams. Xeams has the ability to look for these types of spreadsheets and blocks them from ever entering your end-users inboxes. To learn more about Xeams and how it can help keep your digital work environment safe, as well as its many other useful features, check out our other pages.
Add a comment to this document
Do you have a helpful tip related to this document that you'd like to share with other users?
