How to Prevent ClamAV "Heuristics.Phishing.Email.SpoofedDomain FOUND" for an Email
When using ClamAV, there is a chance that an email gets marked by clamdscan with "Heuristics.Phishing.Email.SpoofedDomain FOUND". This filter looks for HTML links that look suspicious when the display text is a URL that is on a different domain than the actual URL.However, it is very common for a company to contract out web services and to use HTML link display text to make it look like it is a link to the company website, which results in false positives.
For example, a user in your company has sent an email to a client. This email contains a signature, which contains a LinkedIn icon. The client who receives this email can click on this icon, which will go to the company's LinkedIn account. The custom-made icon URL's hostname is mycompany.com, and the hostname of the URL goes to LinkedIn.com.
Since the icon's URL points to mycompany.com and the actual URL goes to a different hostname, ClamAV will mark this as a phishing link. This can result in emails being marked as spam and not delivered to the client's mailbox. There are a few methods for fixing this issue: disabling the phishing scan or adding the hostnames to the whitelist.
Method #1: Disabling URL Phishing Scan in ClamAV
To disable the URL phishing scan feature, please follow the instructions below:- Go to your installation directory for ClamAV.
- Look for a file named clamd.conf. Open this file with a text editor, such as Notepad or Nano.
- Search for the following value: PhishingScanURLs
- To disable URL scanning, set the value to: PhishingScanURLs no
- Make sure the value does NOT start with #, since # indicates it's a comment.
- Save the file and restart Clamd.
Method #2: Whitelisting the address in the Signature Database
Whitelisting the hostname is done by creating a custom database, then specifying this database in the clamscan configuration file. The instructions are below:Creating a whitelist Database file
- Create a file with a .wdb extension. For example: whitelist.wdb
- Open this file with a text editor, such as Notepad or nano.
- In the example earlier, to whitelist the company, add the following line:
M:linkedin.com:mycompany.com - The value can either be the full hostname or a regular expression. Please check ClamAV's documentation here for more details about what values you can specify.
- Save the file and exit.
Specfying the Database file in freshclam
- Go to the installation directory of ClamAV, and look for a file named: freshclam.conf
- Open this file with a text editor, such as Notepad or nano.
- Look for a section that refers to DatabaseCustomURL. Specify the full path of the database file. An example is below:
DatabaseCustomURL file://C:\clamavcustomdatabase\whitelist.wdb
The above specifies the whitelist.wdb is a local file, which is located in C:\clamavcustomdatabase. - Save the file and exit.
- Run freshclam. You should now see the wdb file updated to ClamAV in the command line result, as shown below:
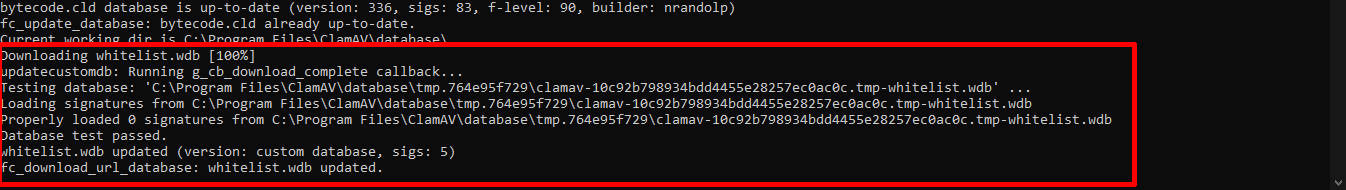
Testing Result
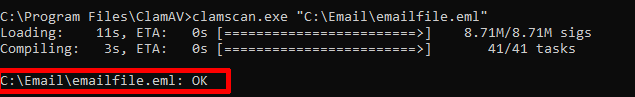
Once either method has been configured, run the clamscan command on an email to confirm that the URL phishing does not apply to the message. Example command is below:clamscan.exe "C:\Email\emailfile.eml"
The result should now show it passes without the filter being applied: